You may have seen a few previous articles of mine on locks; this and this talk about one type of mechanical keysafe. This talks about master keying systems and their inherent vulnerabilities.
I find locks fascinating from an information point of view. And today I’m looking at the human side of these common devices.
You’ll see them all over the place. AirBNB & similar type rentals often have them outside to avoid the owner having to turn up at check-in/check-out. They are used on shared offices to avoid all the users having to have their own key.
I’ve been eyeing these for some time, and in particular looking at the shared access type situation: is it easily exploitable (without shoulder surfing), and are there ways to improve the security around it?
The challenge was to look at the state in which a group of users left the combination after using the keysafe, and see if that left me enough clues to derive the original combination (which I already knew).
Good News, Bad News
The summary of observing the usage gave both good and bad news. The Good News was that no one left the actual combination visible after use. It might be obvious that this should be avoided, but I’ve seen it often enough in other situations for it to be worth noting.
The Bad News was that information does leak, and that with around a hundred observations of different combinations left showing I could narrow the combination down to a very small number of likely candidates and thus break it.
In previous articles, I’ve talked about insiders, outsiders, and nearsiders. The insider risk here arises if this is an area within an organisation’s building which is supposed to be limited to specific users of their own only. The nearsider risk arises if this is an area within a shared office (or similar) where many organisations can get to the keysafe, but the protected area is only for your organisation. The outsider risk arises if the keysafe is publicly accessible. Different situations, different risks.
The Better News is that there are some simple instructions which you can give to the legitimate users of such a keysafe which pretty much eliminate this attack.
The Results
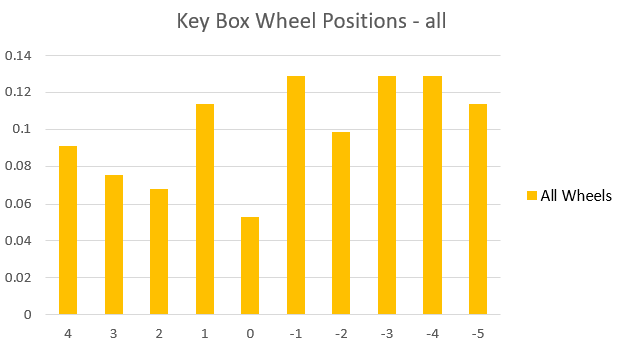
But first, the results. By repeatedly recording the state (that is, the numbers showing) in which the lock was left after use on 35 different occasions, and plotting the delta between the visible number and the combination we can look for patterns.
Probability of a certain offset shown on the Y-axis, offset from the combination value shown on the X-asis (+5 & -5 are the same of course)
Analysis
Looking at the aggregated results across all the wheels, I drew the following conclusion: the least likely place that any wheel is going to be left is on its combination value. This makes sense in terms of human behaviour, but of course it leaks information in the same way as Enigma being unable to encode a letter to itself. With enough samples recorded (estimate about 100 needed, so three times my sample size), I have a high probability of being able to read off the most likely combination from the graphs of individual wheel results, and may need to try a few minor variations.
In the individual wheel graphs, the peaks tended to be one or two either side of the conbination value, plus small peaks at values representing the user setting the number to zero. This latter is interesting, because none of the users were zeroing the entire combination for any of my readings. There was also evidence of less perturbation of wheels 1 & 4 compared with wheels 2 & 3: users just randomly whizzing the wheels around without particularly concentrating on the result understandably tend to move the middle ones more than the edge ones.
Avoid The Leakage
How to avoid the leakage: tell your users to zero the wheel positions after use every time, and nothing leaks. All an attacker can deduce is that your staff are diligent and follow instructions.
Conclusions
Such shared access combination locks tend to have long-lived combinations simply because it is inconvenient to have to inform everyone relevant of a change. They avoid the more obvious signs visible with push-button mechanical locks, and with careful use can avoid leaking the combination.
As with all such situations, you need to consider whether the risk is adequately mitigated by the control. But how a control is used can be important, as demonstrated here.